ping app
Challenge
Look what I’ve learnt! I have even obfuscated it! You can’t possibly find my flag there. No easy points here ;)
https://ping_app.knping.pl/
Overview
Looks like there’s a Flutter app running at the host. We look through the dart.js and see some interesting endpoints.
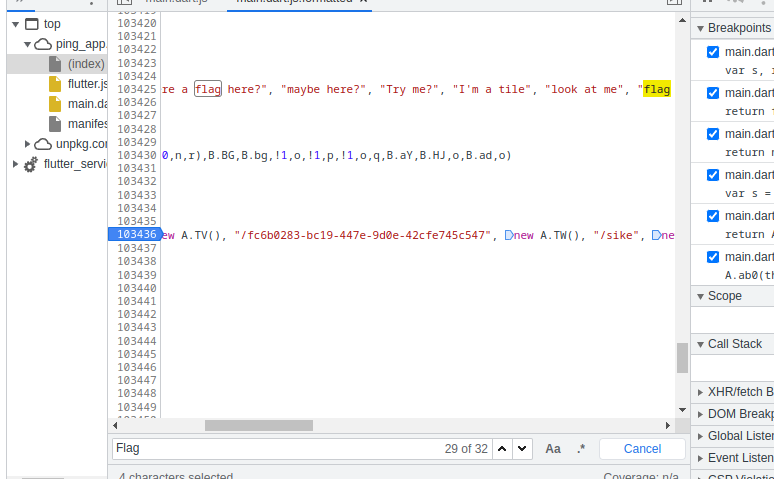
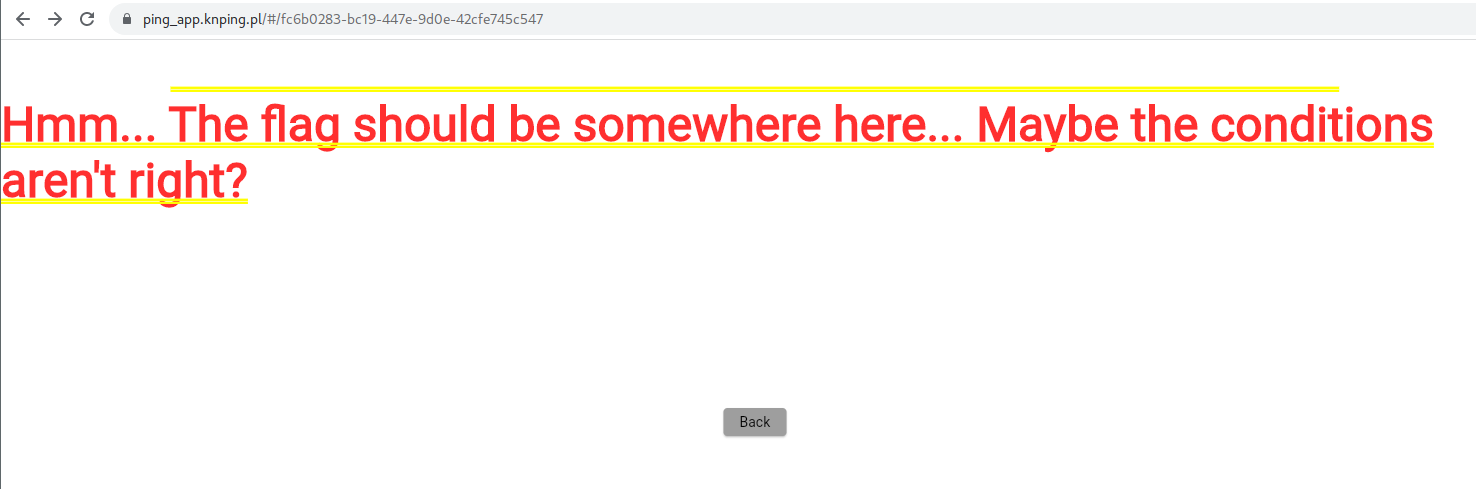
When visiting the uuid endpoint, it looks like we are on the right track:
Debugging
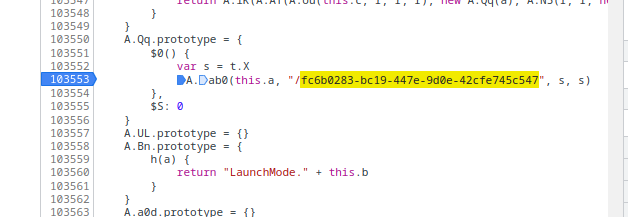
After digging through some of the JavaScript, a stop is set on a function that is hit when access the uuid endpoint.
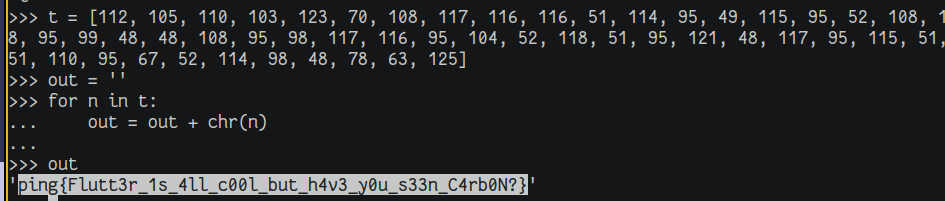
Stepping into the function, we see some obvious data in an array for probable obfuscation.
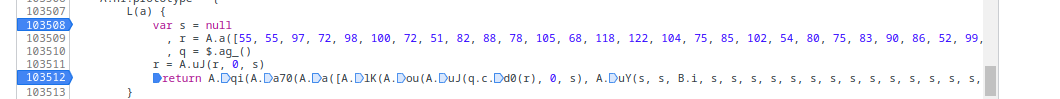
Chasing that data throughout the code, we continue to step through the process and note the array is concatenated:
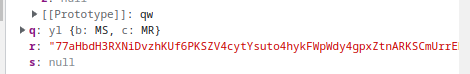
Eventually, the function populates another array with obvious ASCII characters.
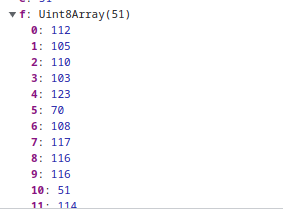
Flag
The suspicious array is copied and the flag is obtained once converted into characters.